
NEW J277 SPECIFICATION
Here you will find easy to follow revision sheets which will help your students to recap the topic:
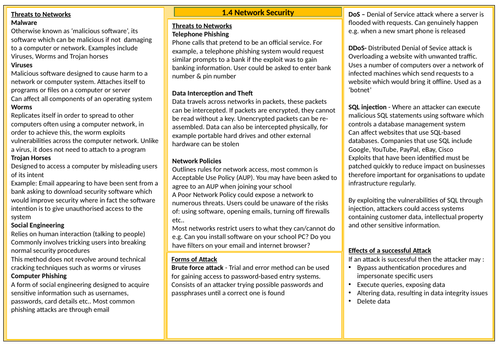
1.4 Network Security
1.4.1 Threats to computer systems and networks ¨ Forms of attack:
o Malware
o Social engineering, e.g. phishing, people as the ‘weak point’
o Brute-force attacks
o Denial of service attacks
o Data interception and theft
o The concept of SQL injection
1.4.2 Identifying and preventing vulnerabilities
¨ Common prevention methods:
o Penetration testing
o Anti-malware software
o Firewalls
o User access levels
o Passwords
o Encryption
o Physical security
Get this resource as part of a bundle and save up to 50%
A bundle is a package of resources grouped together to teach a particular topic, or a series of lessons, in one place.
J277 OCR Computer Science Unit 1 (1.1-1.6) Complete Revision Sheets / Practice Questions
A complete set of revision sheets for J277 OCR Computer Science. Includes all of the topics for the first unit J277/01: Computer systems. 1,1 Systems architecture 1,2 Memory and storage 1,3 Computer networks, connections and protocols 1.4 Network security 1.5 Systems software 1.6 Ethical, legal, cultural and environmental impacts of digital technology With over 150 practice questions to test your students!!!
J277 OCR Computer Science Unit 1 & 2 Revision Pack
The ultimate revision pack for your students to get to grips with the J277 OCR Computer Science specification Includes ALL the resources needed for both unit 1 and unit 2 **Computer Systems** 1.1 Systems architecture 1.2 Memory and storage 1.3 Computer networks, connections and protocols 1.4 Network security 1.5 Systems software 1.6 Ethical, legal, cultural and environmental impacts of digital technology **Computational thinking, algorithms and programming** 2.1 Algorithms 2.2 Programming fundamentals 2.3 Producing robust programs 2.4 Boolean logic 2.5 Programming languages and Integrated Development Environments Save yourself 50% with this bundle :)
Something went wrong, please try again later.
This resource hasn't been reviewed yet
To ensure quality for our reviews, only customers who have purchased this resource can review it
Report this resourceto let us know if it violates our terms and conditions.
Our customer service team will review your report and will be in touch.