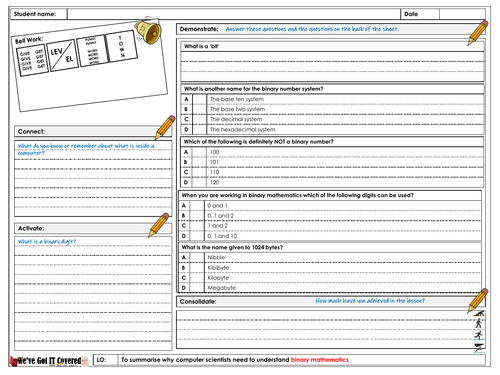
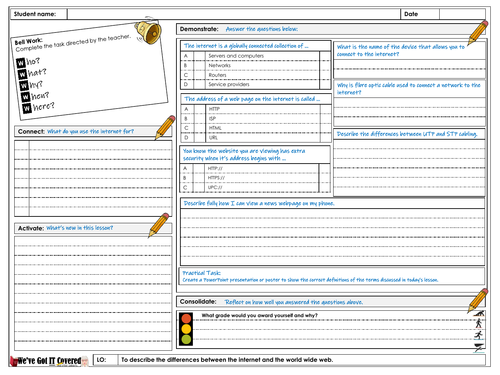
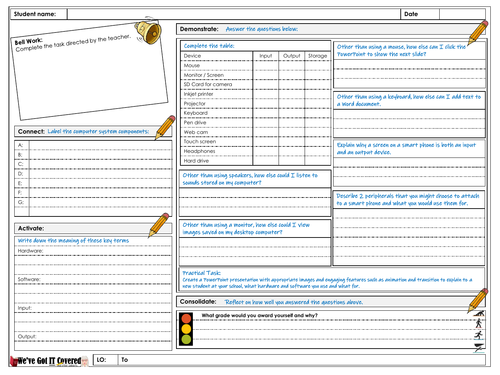
Got IT Covered
Complete units of work, paper based or for lessons with computer access. Individual and stand alone lesson plans that are ideal for cover lessons. All lesson plans and resources are suitable to be taught by a cover supervisor. All lessons identify RWCM links and opportunities to identify careers guidance support. Some include expert teacher commentary but all provide a framework for any teacher to follow. Lesson plans are built using an accelerated learning cycle.